
- About UPF-BSM
- Programs
- Faculty and research
- Companies and Organizations
- News & Events
Understanding how GAFAM are so good at knowing us
2 Noviembre - 2021
Alberto Lempira, Academic Coordinator of the MSc in Marketing
How many times have you thought your devices may be listening to you? The fact is you are not alone. According to a survey by The Independent, around 66% have some suspicious about their devices listening to them, which for some is awesome, yet for some others, plain frighting.
Is this true?
When you look the Terms and Conditions, EULA and Privacy Policy of the GAFAM members (Google, Apple, Facebook, Amazon and Microsoft) they state that some personal information may be used for commercial purposes like advertising, marketing communications, etc. However, some are clearer than others stating if the collection of this information happens on the device or at the “cloud”.
There have been many exposed cases on which some of these companies, and especially their voice assistants have been eavesdropping on their users, in many cases without consent
So, short answer; yes, your device it is at least paying close attention to what you do.
On device data collection
To understand how this happens it is important to note the differences between the data that is collected straight from our devices and the data collected from the cloud. The first gives the opportunity for these firms to understand behavioral aspects that are usually implicit and not explicitly expressed:
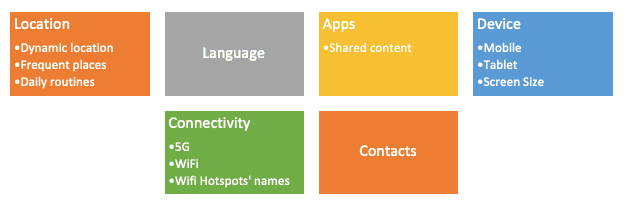
Many of this data points help companies like Facebook to understand what our regular day looks like, and therefore to tag us into an internal classification. This way, if I regularly use public hotspots that require to log in with Facebook to access a Wi-Fi network, they will know that I may be a highly mobile person, or if I move around airports and keep changing cellular networks regularly, they will know that I may be a frequent traveler. All this without me posting or sharing anything on their platform; just by having their mobile app installed with location permissions granted.
Off-device data collection
In addition to the data that can be collected from our devices there are the things these firms may also know because we are actively letting them know: imagine you start browsing for flights to Cambodia, you happen to do that on your mobile phone, at home. The next day you go to work and comment on this vacation you have been planning with your significant other, and later that day you and your coworkers get targeted by campaigns for “cheap flights to Cambodia”; everybody will probably think their smartphones were listening to their conversations, but the truth is a bit disappointing:
Essentially what is happening is that by sharing the same Wi-Fi network on a regular basis with some other people, companies like Facebook or Google may connect the dots, along with the geolocation they could know that on that specific address happen to be based one or several businesses’ offices. Connecting dots even further down the road they may infer that based on location and the fact you and your colleagues use the same network you may work together.
All this, plus the fact that they already have a personal profile of who each one of their users are: their taste, likes and dislikes. But also, the interactions between the users’ account linked to these persons makes the case for they to say:
“This people may be coworkers, so, they must chat about common things”
Whether this is true or not, the algorithm allows them to keep improving by trial and error. But in our example, that would be the suppositions Facebook would make to show you and your coworkers those targeted ads.
But wait, they are really listening to us!
After reading the previous examples we may have a clearer idea of how this targeted campaigning thing happens. Keep in mind that for didactic purposes, this complex process has been overly simplified for this article. But the truth is that there have been many exposed cases on which some of these companies, and especially their voice assistants have been eavesdropping on their users, in many cases without consent.
Whether to ask ourselves if we should do anything to protect our data or just give up to the fact that if we want to have access to free services it is still a thing to be thought
So, let’s be clear. If you use Siri on your Apple devices, and you have the “Hey Siri” feature ON, these devices will be actively listening for the trigger command; the same happens with Amazon’s Echo and Alexa or with Google’s devices and the Google Assistant.
With that being said. The users should grant express permission for this companies to keep a stored record of the conversations and voice recordings on their servers. This was, however, not the case of Apple for quite a while.
A report from The Guardian back in 2019 showed that some Apple contractors had access and listened to multiple recordings from users that ranged from them talking about medical information to them having sex with their partners. All this for the purpose of improving quality and to grade the efficiency of the voice assistant.
This was however, not disclosed back then to the users, who accepted the terms and conditions to use Siri without knowing what information they were giving away. Apple apologized for this mistake and decided to turn this feature off by default, and now users must explicitly accept this.
Apple was not the only one committing this kind of mistakes. Amazon also had issues with unauthorized users’ recordings, and even further, in an article from The Verge on 2018 citing German magazine c’t; Amazon send by mistake 1.700 recordings to the wrong user after a personal data request (something all the European citizens have access to, in part thanks to the GDPR) putting the company in the middle of a scandal for the bad management of personal and sensitive data from their users.
We must know what information breadcrumbs are we leaving behind, and most importantly, how to avoid giving out really sensitive information we may not want for them to have.
Is there anything we can do?
Whether to ask ourselves if we should do anything to protect our data or just give up to the fact that if we want to have access to free services it is still a thing to be thought. However, what surely will make a difference on protecting the personal data that we put out there for companies like GAFAM to have been to understand the sources of these data points.
Nowadays, apps from companies like Facebook have over 52.000 data points per user according to KimKomando. That means that most probably the only way to avoid them to have access to any information from us is staying out of the grid. But this is not realistic for most of the internet users.
So we must know what information breadcrumbs are we leaving behind, and most importantly, how to avoid giving out really sensitive information we may not want for them to have.
